Modular Inspection Network Xfer Agent (minx)
Introduction
minx is a command line tool that runs on an endpoint target machine, acting as an agent to collect data from the endpoint and send it a central forensics workstation running the nx tool. Therefore, to understand minx, one needs to understand nx.
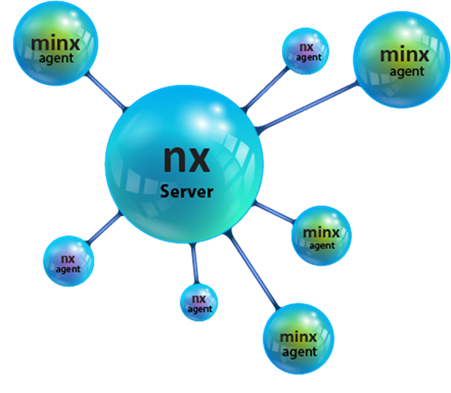
As background, the nx tool can act as both a client and server for the purposes of transferring data from more than one computer (acting as clients) to a central computer (acting as the server). The central computer, in this case, would be the forensic workstation gathering information during an incident response collection. The clients would be those computers that are under investigation. minx and nx clients can co-exist and both work with an nx server as shown below
Like many of the TZWorks tools, when nx runs, it needs a valid license file to be resident in the location where nx is run from. When operating in a client mode, the nx client capabilities are limited to just standard file copying and/or piping output from another tool. Any scripting of the nx client in performing multiple operations require one to use a batch file or shell script, where each command would invoke a separate instance of the nx client. In this scenario, multiple instances of nx would be running at the same time; one for the server, and a separate instance for each client.
Some agent enhancements minx incorporates over nx, includes:
-
- An integrated NTFS engine to allow minx to copy any file from a target Windows computer by accessing the file data via raw cluster reads
- The ability to scan all drives attached to a target computer (to get volume offset sizes, gaps in the disk, etc)
- The ability to image or copy any sectors from a specific drive
- An internal directory enumerator with optional filtering to target specific files within one, or a group, of subdirectories
- Can spawn other applications or tools available on the target machine and send their output directly to the nx server
- Embedded internal scripting engine that allows it to receive instructions (via a simple text file) from the nx server.
The minx scripting capability allows any of functionality list above to be packaged into a script to be acted on in one session. These scripts can be run locally manually from the endpoint or automatically, via stored scripts on the nx server side. For the latter option, one can configure minx to query the nx server for any available script to be forwarded to it. Once minx receives a script from the nx server, it will immediately execute it. So if you wanted to pull the $MFT file, all the registry hives, event logs, or spawn your favorite tool resident on the endpoint computer, it can be easily scripted and given to minx to execute on a live endpoint. All data collected by minx, in this way, is encrypted and sent to the central forensics workstation running nx.
For more information
For details on its capabilities and how to use them, the user's guide can be viewed here: here
If you would like more information about minx, contact us via email.
Downloads
| Intel 32-bit Version | Intel 64-bit Version | ARM 64-bit Version | ||||
| Windows: | minx32.v.0.29.win.zip | minx64.v.0.29.win.zip | minx64a.v.0.29.win.zip | md5/sha1 | ||
| Linux: | minx32.v.0.29.lin.tar.gz | minx64.v.0.29.lin.tar.gz | minx64a.v.0.29.lin.tar.gz | md5/sha1 | ||
| Mac OS X: | Not Available | minx.v.0.29.dmg | minx.v.0.29.dmg | md5/sha1 | ||
| *32bit apps can run in a 64bit linux distribution if "ia32-libs" (and dependencies) are present. | ||||||