Volume Shadow Snapshot Enumerator (vssenum)
Introduction
vssenum is a command line tool that only works on Windows and its purpose it to enumerate the Volume Shadows on the host machine.
The purpose of this tool was not to recreate the built in vssadmin utility that is part of the Window OS, but to have something that could assist in testing out our other tools (via scripting) that were Volume Shadow aware.
How to use vssenum
There are 4 options for the Volume Shadow Snapshot enumerator: (a) display volume shadow statistics, (b) display only volume shadow symbolic links and (c) display volume shadow snapshot indexes. Below is the menu:
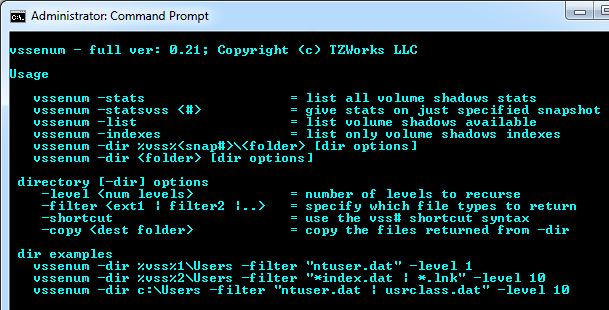
Displaying Volume Shadow Statistics
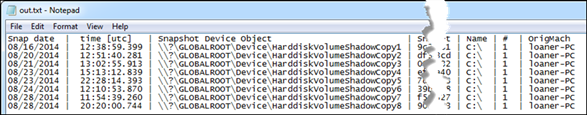
Listing the available Snapshots
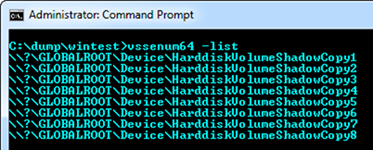
Directory enumeration within a Snapshots
Below are 2 examples using different options to pull both the ntuser.dat and usrclass.dat hives from volume shadow snapshot #2. The -filter option allows one to add multiple filters to the directory enumeration, which in this case are the user hives. The first example uses the -shortcut option, while the second does not. If used in conjunction with another tool one can easily script the output of vssenum to give one the control to process the desired file(s).
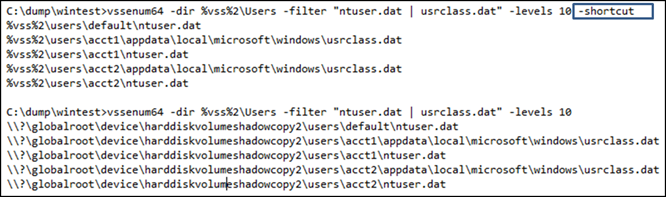
Using vssenum in a script
One problem with pulling artifacts from volume shadows is finding which shadow copies are available on the system in question. Once this is known, one can read the desired volume shadow using the device object name of the volume shadow. Encapsulating this enumeration within a script and pulling the requisite data can cause some convoluted scripting. vssenum makes scripting of the enumeration of shadow copies much easier.
For example, using the -indexes option, one can take the output of vssenum and feed it into another tool to parse some artifact. Below is a useful script that does this and is tailored to work for a number of TZWorks tools that are volume shadow aware.
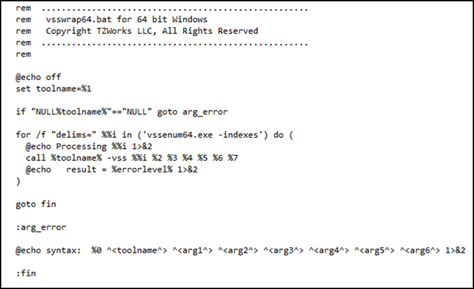
The -dir option is also smart enough to enumerate mounted volumes that are not volume shadows; just substitute the %vss%<snap#> with the drive letter.
Assume the above script is named vsswrap64.bat. Below are examples of using this script to parse a certain artifact from all the volume shadows on a system.
// for sbag
vsswrap64 sbag64 -csv > sbag.results.csv
// for jp
vsswrap64 jp64 -csv > jp.results.csv
// for lp
vsswrap64 lp64 -csv > lp.results.csv
// for jmp
vsswrap64 jmp64 -csv > jmp.results.csv
// for usp
vsswrap64 usp64 -csv > usp.results.csv
...
For more information
The user's guide can be viewed here
If you have any questions about vssenum, contact us via email.
Downloads
| Intel 32-bit Version | Intel 64-bit Version | ARM 64-bit Version | ||||
| Windows: | vssenum32.v.0.39.win.zip | vssenum64.v.0.39.win.zip | vssenum64a.v.0.39.win.zip | md5/sha1 | ||
| Linux: | Not Available | Not Available | Not Available | |||
| Mac OS X: | Not Available | Not Available | Not Available | |||
| *32bit apps can run in a 64bit linux distribution if "ia32-libs" (and dependencies) are present. | ||||||