Computer Account Forensic Artifact Extractor (cafae)
Introduction
cafae is a Windows registry parser that targets specific registry keys that help identify user activity as it pertains to files and program execution. Chosen are a handful of registry entries that are specific to an account's registry hive(s). This includes both a user's ntuser.dat hive and the usrclass.dat hive for Vista and later. Collectively, these two registry hives contain artifacts useful in piecing together some sort of file/program activity that occurred on a specific account. The newer versions of cafae extended the report generation to the software, system, security and amcache hives.
Why build another Windows registry parser when there are plenty of good registry parsers freely available on the Internet? The answer is simple. We listened to the feedback that was submitted to our shop by the forensics community, specifically to take some of the yaru functionality and make an easy to use command line tool. The desire was to be able to use it in a batch processing mode while outputting the data into one of the more common formats so that it could be 'somewhat easily' fused together with varying artifacts from other sources.
cafae consists of the same parsing engine that is in yaru packaged into a console application. Consequently, the reports that are generated will look similar to those of yaru's, but will have more output options, such as a couple of CSV variants, the ability to change the date format, ability to set the time precision, and others.
Other useful aspects of cafae include the following:
- a. Can parse hives from a live system (same as yaru). Can easily parse hives from Volume Shadow copies on a live system.
- b. Is ubiquitous across WinXP and Win8 (meaning it figures what version of the hive it is working on and then automatically adjusts which registry keys should be used).
- c. In some cases, it can parse deeper into the metadata and pull out additional artifacts than current registry parsers available.
- d. Non-Windows versions are available for those that choose to process Windows artifacts on a non-Windows operating system.
- e. The architecture is extremely extensible to include additional registry subkeys.
- f. Exposes a scripting engine so one can pull any registry artifact one wishes with minimal effort.
- g. Has a registry subkey carving option to pull out keys from corrupted hives.
How to use cafae
cafae is a console application that targets user registry hives (eg. ntuser.dat and usrclass.dat files), as well as, software, system, and security hives. To use this tool on a live system, one will need to open the command prompt with administrator privileges first. One can display the menu options by typing in the executable name with no parameters. A screen shot of the menu is shown below. The menu groups the available artifacts by area of analysis, where each artifact can be extracted independently or combined per command issued. If an artifact comes from a specific type of user hive, the option will identify which hive (either ntuser.dat or usrclass.dat) it expects to receive as input for it to successfully extract data.
The user registry artifacts are grouped into the categories: (a) running a program, (b) opening files, (c) searching/browsing and (d) network/computer settings, etc. The report generation for the operating system hives (eg. software, system and security) have separate options respective to those hives. The output options include: (a) the default output, where each record is on a separate line and each field is separated by the pipe character, (b) the SleuthKit body-file format and (c) the log2timeline CSV (comma separated value) format.
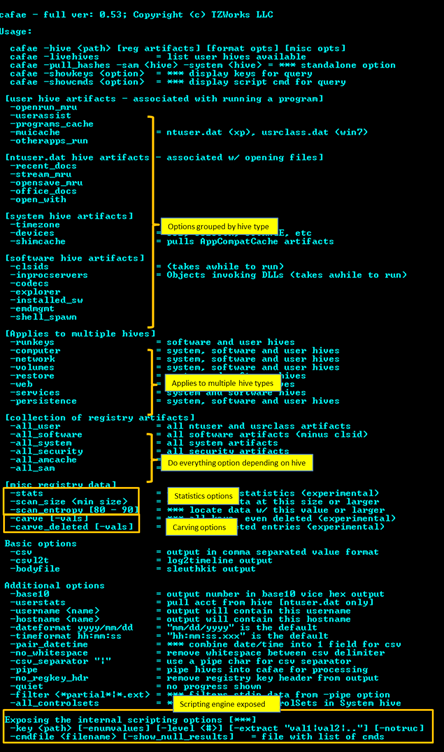
To process a specified user hive, one uses the -hive <location of hive to process> option with the specific artifact one is interested in. For example, assuming a user hive was extracted to the c:\dump directory, one could review all the Microsoft Office documents accessed by this user by typing:
cafae -hive c:\dump\ntuser.dat -office_docs > office_docs.txt
Since the output that is generated is very wide, it is recommended that one redirect the output of the command into a file as show above. Then it can be reviewed in any text editor by turning off the word wrap option to view each record on a separate line.
Example Artifacts that are Extracted and Parsed
As a disclaimer, this version of cafae does not contain all the requisite registry keys that may be of interest to a computer forensic analyst, but it does encompasses some of the more common ones. Furthermore, every attempt has been made to ensure that this tool parses data correctly; however, there may be cases where the data parsing fails. If this happens, please send a note to: info@tzworks.com.
Below are examples of some of the registry artifacts cafae can extract. Each subsection includes which registry keys are examined, the command line syntax that was used, and when available, a sample output with annotations.
Open -> Run Dialog
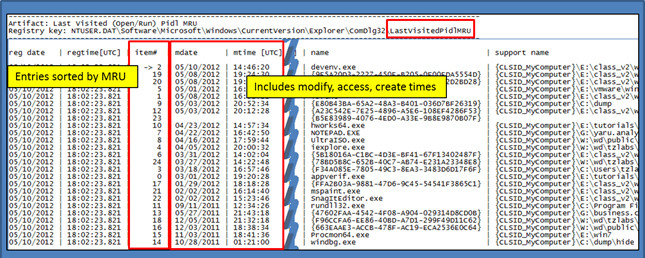
- ntuser.dat\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\LastVisitedMRU
- ntuser.dat\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\LastVisitedPidlMRU
- ntuser.dat\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\LastVisitedPidlMRULegacy
These keys track the program that was last used to access the files listed in the Open/Save dialog box MRU subkey. With Vista and later, most of these entries record the timestamp of when the program was executed. The MRU (Most Recently Used) value will show the order of the entries, from the most recently used. cafae makes use of this MRU value to sort the output from most to least recently accessed.
Example: cafae -hive user.win7.hive -openrun_mru > out.txt
UserAssist Key
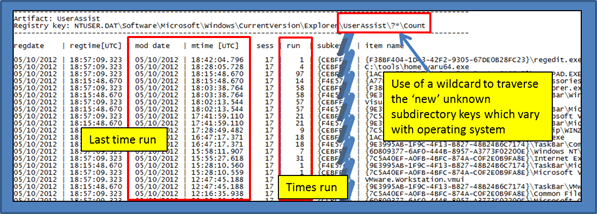
- ntuser.dat\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist
This key contains values that identify programs executed by a user account. Entries are a mix of executable files and an associated link entry. Many of the entries contain the last execution time along with the number of times the application was run. While the last execution time seems reliable, the run count data is still under evaluation and is based on empirical data. Therefore the results of this output should be considered experimental.
Example: cafae -hive user.win7.hive -userassist > out.txt
ProgramsCache Key
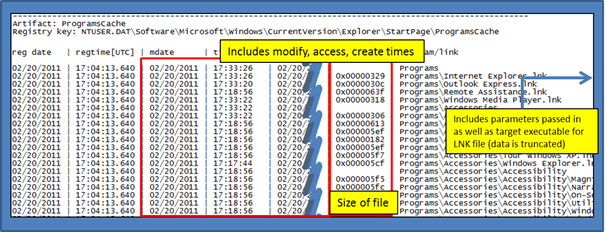
- ntuser.dat\Software\Microsoft\Windows\CurrentVersion\Explorer\StartPage\ProgramsCache
- ntuser.dat\Software\Microsoft\Windows\CurrentVersion\Explorer\StartPage2\ProgramsCache
- ntuser.dat\Software\Microsoft\Windows\CurrentVersion\Explorer\StartPage2\ProgramsCacheTBP
- ntuser.dat\Software\Microsoft\Windows\CurrentVersion\Explorer\StartPage2\ProgramsCacheSMP
The ProgramsCache key records which application was launched as well as when it was launched. The size of the file refers to the link file and not the target file the link points to. Not shown in the diagram below, but included in the truncated section on the right, are additional parameters that may have been present in the data.
Example: cafae cafae -hive user.winxp.hive -programs_cache > out.txt
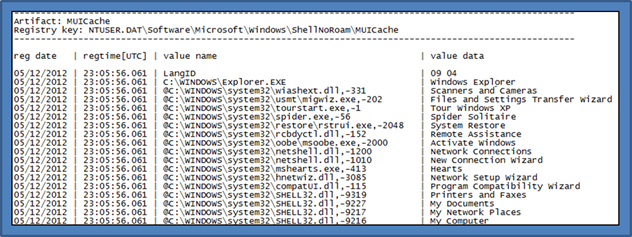
MUICache Key
- ntuser.dat\Software\Microsoft\Windows\ShellNoRoam\MUICache
- usrclass.dat\Local Settings\Software\Microsoft\Windows\Shell\MuiCache
The operating system records what applications are launched by a particular user account. The MUIcache subkey records the name of the application and the File Description information. This description is taken from the version information stored in the portable executable of the binary that was launched. Unfortunately, there is no execution timestamp information associated with each entry.
Example: cafae -hive user.winxp.hive -muicache > out.txt
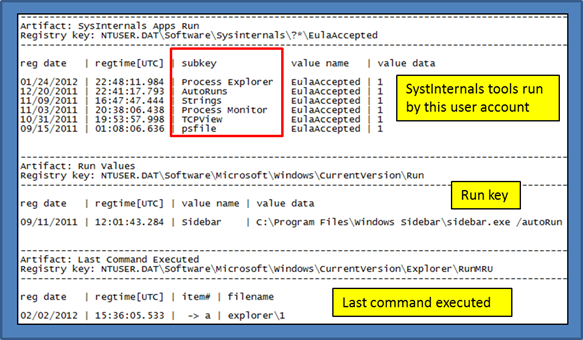
Run Key and Miscellaneous Applications
- ntuser.dat\Software\Microsoft\Windows\CurrentVersion\Run
- ntuser.dat\Software\Microsoft\Windows\CurrentVersion\Run\?*\
- ntuser.dat\Software\Microsoft\Windows\CurrentVersion\RunOnce
- ntuser.dat\Software\Microsoft\Windows\CurrentVersion\Explorer\RunMRU
- ntuser.dat\Software\Sysinternals\?*\EulaAccepted
The Run and RunOnce registry keys cause programs to run each time that a user logs on. It is a common and well known way for applications to remain persistent across reboots.
For this example, however, we highlighted the SysInternals subkey along with its EulaAccepted value. If the value is set to a 1, then the user accepted the EULA and the tool ran. This is a good way to tell which SysInternals tools have been run on the system.
Example: cafae -hive user.win7.hive -otherapps_run > out.txt
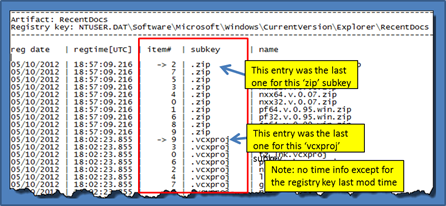
Recent Documents and Associated Keys
- ntuser.dat\Software\Microsoft\Windows\CurrentVersion\Explorer\RecentDocs
- ntuser.dat\Software\Microsoft\Windows\CurrentVersion\Applets\?*\Recent [File List]
- ntuser.dat\Software\Adobe\?*\?*\AVGeneral\cRecentFiles\?*\tDIText
- and others ...
For the standard 'Explorer\RecentDocs' item, this key contains the recent documents as identified in the Windows "My Recent Documents" menu. Within the key is a MRUListEx value that identifies the most recently viewed items. If one parses the MRUListEx, one can display the items in the order that they were accessed relative to each other. cafae will output this list of items in the proper order starting with the most recently viewed first. While there is no temporal information associated with each entry, one can use registry last modification time associated with the subkey to determine when the most recent item was opened.
Example: cafae -hive user.win7.hive -recent_docs > out.txt
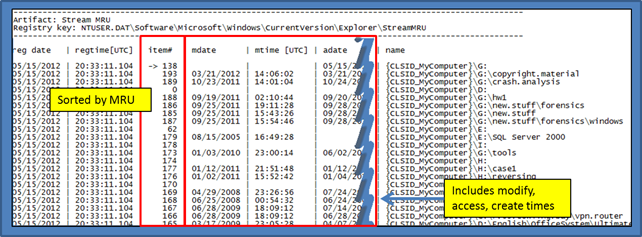
StreamMRU Key
- ntuser.dat\Software\Microsoft\Windows\CurrentVersion\Explorer\StreamMRU
Per the MSDN article 235994, the Streams registry entries store the size and location information for closed windows. The article states that Windows saves this information for up to 28 different windows. The association for the Streams subkey with a particular window is stored in the StreamMRU subkey. As one can see there are embedded timestamps for many of the entries.
Example: cafae -hive user.winxp.hive -stream_mru > out.txt
Open -> Save Dialog
- ntuser.dat\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\OpenSaveMRU/?*/
- ntuser.dat\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\OpenSavePidlMRU/?*/
The operating system tracks files that have been opened or saved from an "Open/Save As" shell dialog box through these registry keys. They contain multiple subkeys that represent different extensions. Each subkey that represents an extension contains values sorted by a MRU list. With Vista and later, most of these entries record the timestamp when the action occurred. cafae sorts these entries by folder subkey and then by most recently used. The output includes an arrow to designate which item was the last one modified.
Example: cafae -hive user.win7.hive -opensave_mru > out.txt
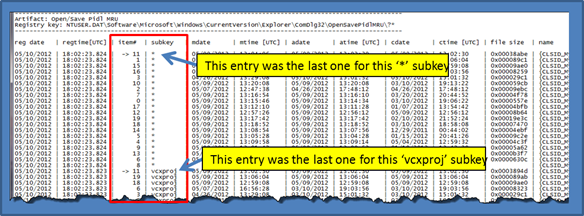
Keys Associated with Office Documents
- ntuser.dat\Software\Microsoft\Office\?*\?*\Recent Files
- ntuser.dat\Software\Microsoft\Office\Office\?*\?*\File MRU
- ntuser.dat\Software\Microsoft\Office\Office\?*\?*\Place MRU
- and others ...
Per the MSDN article 826208, many Microsoft Office programs maintain a list of the most recently used (MRU) files. Additionally, the various Office programs display this MRU list on the File menu and in several other locations. These locations include the Open dialog box, the Save As dialog box, and the Insert Hyperlink dialog box. The purpose of this feature is to provide quick access to files that a user is working on. When extracting this data from the relevant subkeys, one will be able to not only see the file that was used, but the actual timestamp it that file was accessed.
Example: cafae -hive user.win7.hive -office_docs > out.txt
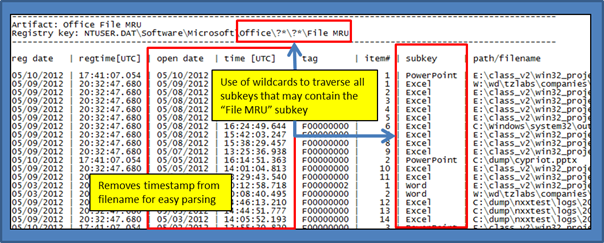
OpenWithList Key
- ntuser.dat\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\?*\OpenWithList
The OpenWithList artifact has a separate subkey for each extension of a file that was opened. Within each extension subkey, the list associates which application is used to open a file with that specific extension. Each of the items within an extension is ranked by a letter, which indicates the order of application execution.
Example: cafae -hive user.win7.hive -open_with > out.txt
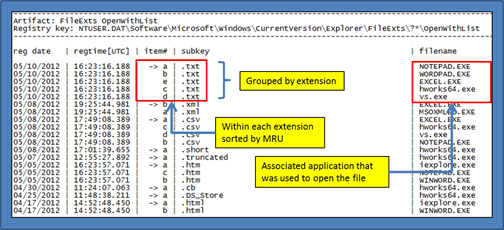
ShellBag Keys
For completeness this important set of registry keys is just mentioned here. This option, however, was not made available with cafae, since the sbag tool was developed to specifically parse these registry artifacts.
Search History
- ntuser.dat\Software\Microsoft\Search Assistant\ACMru
- ntuser.dat\Software\Microsoft\Windows\CurrentVersion\Explorer\WordWheelQuery
For Windows XP there is the ACMru key, which stores search terms that have been typed into a Windows search dialog box. The following subkeys define where the search term was used:
- 5001 - List of terms used for the Internet Search Assistant
- 5603 - List of terms used for the Windows XP files and folders search
- 5604 - List of terms used in the "word or phrase in a file" search
- 5647 - List of terms used in the "for computers or people" search
Unfortunately, Vista did not include a registry key for user searches. Windows 7, however, defines the WordWheelQuery subkey to record information about user searches. Below is an example of the WordWheelQuery data.
Example: cafae -hive user.win7.hive -search_history > out.txt
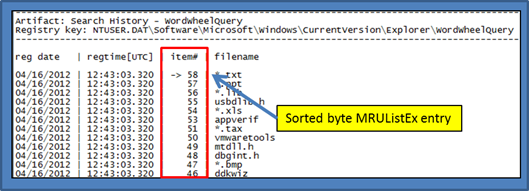
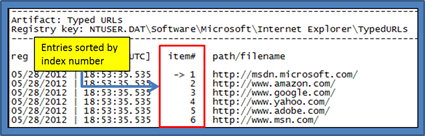
TypedURLs key
- ntuser.dat\Software\Microsoft\Internet Explorer\TypedURLs
When a user types (or adds via a copy/paste) a URL directly into the browser, the TypedURLs subkey is updated. The list of URLs is sorted by number. The lowest number is the last (or most recently typed) URL.
Example: cafae -hive user.win7.hive -typed_urls > out.txt
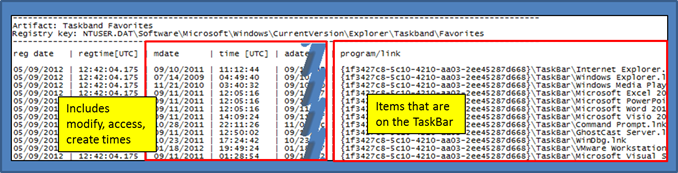
Favorites key
- ntuser.dat\Software\Microsoft\Windows\CurrentVersion\Explorer\StartPage\Favorites
- ntuser.dat\Software\Microsoft\Windows\CurrentVersion\Explorer\StartPage2\Favorites
- ntuser.dat\Software\Microsoft\Windows\CurrentVersion\Explorer\Taskband\Favorites
This set of keys covers the shortcuts on the Windows Start Menu and the TaskBar, respectively. Shown below, is an example of the parsed output of the TaskBar shortcuts. Some of the data in the figure is truncated to the right of the output. The truncated data includes extra metadata that was available that could be parsed out.
Example: cafae -hive user.win7.hive -favorites > out.txt
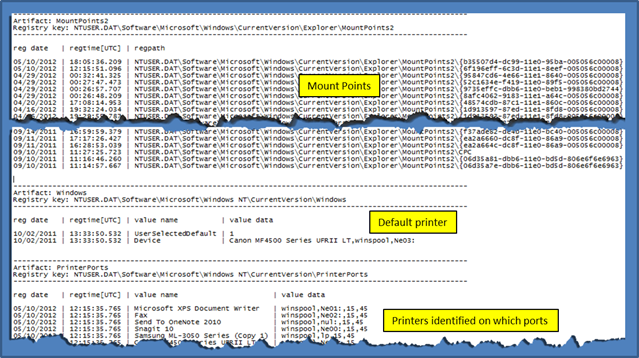
Miscellaneous Metadata
- ntuser.dat\Software\Microsoft\Windows\CurrentVersion\Explorer\MountPoints2
- ntuser.dat\Software\Microsoft\Windows\CurrentVersion\Explorer\Map Network Drive MRU
- ntuser.dat\Software\Microsoft\Windows\CurrentVersion\Explorer\ControlPanel
- ntuser.dat\Software\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders
- and others ...
This last subsection is just a catch all for other useful artifacts that pertain to the computer configuration as set by (or indirectly affected by) the user.
Example: cafae -hive user.win7.hive -computer > out.txt
For more information
The user's guide can be viewed here
If you have any questions about cafae, contact us via email.
Downloads
| Intel 32-bit Version | Intel 64-bit Version | ARM 64-bit Version | ||||
| Windows: | cafae32.v.0.80.win.zip | cafae64.v.0.80.win.zip | cafae64a.v.0.80.win.zip | md5/sha1 | ||
| Linux: | cafae32.v.0.80.lin.tar.gz | cafae64.v.0.80.lin.tar.gz | cafae64a.v.0.80.lin.tar.gz | md5/sha1 | ||
| Mac OS X: | Not Available | cafae.v.0.80.dmg | cafae.v.0.80.dmg | md5/sha1 | ||
| *32bit apps can run in a 64bit linux distribution if "ia32-libs" (and dependencies) are present. | ||||||