Portable Executable Scanner (pescan)
Introduction
pescan is a command line tool to scan portable executable (PE) files to identify how they were constructed. Various metadata is displayed, identifying items such as:
-
- Compile timestamp
- MACB timestamp
- File size and type of executable
- Target OS and whether binary is 32 or 64 bit
- Linker version used
- Entry point address and desired image base address
- Whether an X509 certificate was used and who the author is
- Whether there is a checksum present and does it match the binary
- Optional analysis of the PE internals to generate an abormality score which compares the internal construction to the standard operating system files. Higher scores equate to larger differences.
- Optional MD5 and/or SHA1 hashes of the file can be generated as part of the scan.
As an option, one can also use any standard PEiD signature file and pass it to pescan during its scan. Additional statistics will be displayed based on the PEiD signatures found. One can use this option to generate one's own signatures to help identify certain classes of binaries, instead of just using it to identify compiler version and/or packer version.
Internally, pescan uses the same PE libraries that are used in pe_view to analyze and display the PE internals. Like pe_view, pescan uses cross platform C++, and hence, there are compiled versions for Windows, Linux and OS-X, both in 32 and 64 bit binaries.
How to use pescan
The command menu shows most of the options available. pescan can operate on: (a) a single PE file or (b) a collection of PE files using the -pipe option. The ability to process many PE files in one session was what pescan was designed for.
When processing many files in one session, if one uses the default output (which is not the CSV option), it results in a formatted display which is easy to read in any text editor, since the fields are reasonably spaced to allow for better viewability. This default option also has the benefit that it uses pipes as delimiters which means there is no chance of namespace collision with filenames should one want to import this file into Excel. On the other hand, if one uses the CSV option, the individual fields are packed between comma delimiters. This is most useful for spreadsheet applications and less useful for text editors to view the data. Below is an example of the default output.
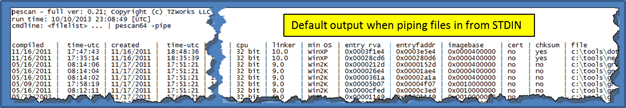
There are two basic forms of output: (a) unstructured text, displaying multiple lines per PE file analyzed and (b) structured, delimited text, displaying one line per PE file that is analyzed. The output is really a function whether one is analyzing one file or many files in one session. For single file analysis, the output will be unstructured, multi-lined format as shown below.
PEiD signature mode
PEiD is a separate GUI tool used to scan and detect common packers, cryptors and compilers for PE files. A reference about PEiD can be found here. PEiD has three main scanning modes: (a) Normal mode - which scans the PE file at its entry point for all defined signatures, (b) Deep Mode - which scans the PE file section containing the entry point, and (c) Hardcore Mode - which does a complete scan of the entire PE file.
pescan can make use of the PEiD signature file and perform similar scans as PEiD, using the -peid <signature file> option. As the default, pescan operates in what PEiD calls the 'normal mode', which only scans the entry point of the PE file. See the readme on how to scan in the other modes.
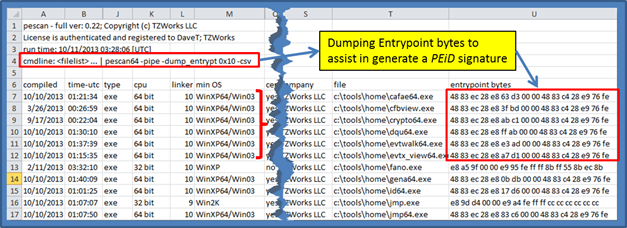
Many PEiD signature files are available for download via the Internet, and unfortunately, many of them are dated. Therefore to assist one in generating one's own set of signatures that can be incorporated in a signature type file, pescan has an option to dump the bytes of the entry point of the file under analysis. This option is -dump_entrypt <# bytes>. Using this option, one is limited up to 80 bytes to be dumped as part of the output. Armed with this data, one can generate their own entry point signatures. See the snapshot below, to see how the data is presented to the user.
Computing a hash and Anomaly Detection
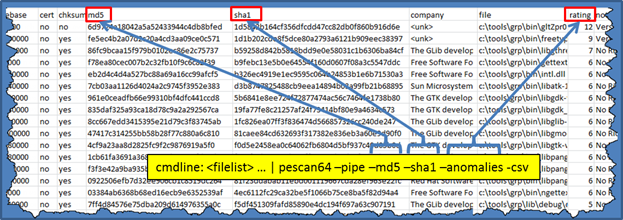
Sometimes one wishes to identify a PE file in a way to compare it with other databases that collate binary hashes. To aid in this, pescan can either compute the MD5 hash or SHA1 hash or both using the options -md5 and -sha1 separately or together. The hash is added as a separate field in the output displayed.
In addition to that hashing options, pescan has what we call 'abnormality detection'. In the context of pescan, this consists of looking at the PE file structure/packing and comparing it to what normally is available with a Windows operating system executable, dynamic link library or driver file. Based on the differences found, a score is assigned. The higher the score, the more differences were found in the construction of the binary file under analysis from the norm. Furthermore, a high score does not mean the binary is malware or malicious, it just means it was constructed using tools and/or methods that are different than what was normal to other Windows operating system files. It could be that the author of the binary wanted to obfuscate the internals of the file from reverse engineers, or it could have been built from some non-standard compiler/linker. If there was a high score assigned to a binary, one needs to also look at the reasons for the high score.
Here are a handful of things pescan looks at during an anomaly scan while making a determination of the score.
-
- Is the entry point in a standard location or not
- Does the binary make use of thread local storage
- Is the import table present
- Does any of the sections in the binary have high entropy
- Are any of the binary section headers abnormal
- Was there evidence of internal strings being obfuscated
- Were the exports obfuscated
- Was there a checksum mismatch
- Do any resources contain possible embedded executable files
- Was there evidence of binary patching
- Was any of the resources modified after compilation
- etc
Below is a sample output using both hashing options and anomaly detection. The output is sorted in descending anomaly scores. If a binary scored a high rating, then one can either analyze the file in more detail using other tools available or just submit the MD5/SHA1 hash to Virus Total, Bit9 FileAdivsor or some other service for their take.
Extraction of Message & Template Tables from select PE filesh
Since pescan focuses on the analysis and reporting of PE internals, the extraction options are limited (pe_view has much better extraction options). However, for the case of message tables and message templates, we included the extraction capability into pescan as well.
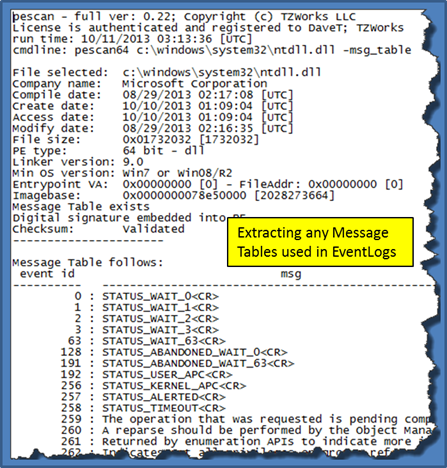
As background, message and template tables are used to map event identifiers to some message. Windows services and drivers use these tables in conjunction with the event log service to record noteworthy events. We found it useful for our internal development to have a command line tool to extract these tables to assist in our development and hence the inclusion into pescan.
To use this option, one uses the appropriate command switch: -msg_table or -wevt_temp. These options will cause the output to be rather verbose, and thus, cannot be used with the CSV output.
Below is an example of extracting the message table from the Windows ntdll.dll file. Performing this on select PE files (those that contain message/template tables), one can create a complete mapping of event identifiers to messages.
For more information
The user's guide can be viewed here
If you would like more information about pescan, contact us via email.
Downloads
| Intel 32-bit Version | Intel 64-bit Version | ARM 64-bit Version | ||||
| Windows: | pescan32.v.0.66.win.zip | pescan64.v.0.66.win.zip | pescan64a.v.0.66.win.zip | md5/sha1 | ||
| Linux: | pescan32.v.0.66.lin.tar.gz | pescan64.v.0.66.lin.tar.gz | pescan64a.v.0.66.lin.tar.gz | md5/sha1 | ||
| Mac OS X: | Not Available | pescan.v.0.66.dmg | pescan.v.0.66.dmg | md5/sha1 | ||
| *32bit apps can run in a 64bit linux distribution if "ia32-libs" (and dependencies) are present. | ||||||